Bongo Security is a worldwide operating Cyber Security Consulting firm. It was established by leading industry experts and provides Vulnerability Assessments, Ethical Hacking, Penetration Testing, Open Source Intelligence (OSINT) and Cyber Awareness Training.
“There are two types of companies: those that have been hacked, and those who don’t know they have been hacked.”
John Chambers, Former CEO, Cisco Systems
We serve both private sector and government clients in more than 30 countries and have a local presence in all major business hubs in the Americas, Europe and Asia. Our customers come from all verticals and sizes. Our job is to discover IT security holes and vulnerabilities in customer networks and systems in order to protect IT infrastructures from ever more increasing threats and attacks in Cyber space.
What is Penetration Testing?
A Penetration Test is a method of evaluating computer and network security by simulating an attack on a computer system or network from external and internal threats. The same tools, know-how and methodologies are being used, as malicious hackers would employ. The difference to a real attack is the fact that testing is done with the explicit written consent of the client and the purpose is to produce a comprehensive report and to close down security holes, before a real attacker can exploit them.
Why Penetration Testing?
![]() Many Compliance regulations demand regular Penetration Testing
Many Compliance regulations demand regular Penetration Testing
![]() What if a competitor or hacker would steal your digital assets?
What if a competitor or hacker would steal your digital assets?
![]() What legal consequences would a security breach have for you?
What legal consequences would a security breach have for you?
![]() What would be the financial implications if your systems are taken down?
What would be the financial implications if your systems are taken down?
![]() What reputational damage would a breach pose to your business?
What reputational damage would a breach pose to your business?
![]() Did you know that 90% of all deployed IT systems have vulnerabilities?
Did you know that 90% of all deployed IT systems have vulnerabilities?
![]() Automated scanners cannot many modern vulnerabilities such as IDORs and business logic flaws
Automated scanners cannot many modern vulnerabilities such as IDORs and business logic flaws

Why Bongo Security?
![]() We are experts in Penetration Testing and Ethical Hacking
We are experts in Penetration Testing and Ethical Hacking
![]() We are an independent third party concerned with finding & fixing flaws
We are an independent third party concerned with finding & fixing flaws
![]() No conflict of interest. We are not embedded with HW/SW vendors
No conflict of interest. We are not embedded with HW/SW vendors
![]() Consultants holding the highest industry and government certifications
Consultants holding the highest industry and government certifications
![]() Experience across all sectors and business sizes
Experience across all sectors and business sizes
![]() Dedicated Red Team approach with specialists in all technologies
Dedicated Red Team approach with specialists in all technologies
![]() Using international testing frameworks such as OWASP, NIST, SANS etc.
Using international testing frameworks such as OWASP, NIST, SANS etc.
![]() Your Security is our Priority!
Your Security is our Priority!
Leveraging Bug Bounty Expertise
Many of our consultants are actively engaged in public and private bug bounty programs for brands like Amazon, Twitter, Facebook, Google, Uber, LinkedIn, the U.S. Department of Defense and others. These are often seasoned and extremely hardened systems and applications, yet our consultants discover and report high impact flaws in these companies on a regular basis. We are leveraging our bug bounty expertise on hardened systems and applications in our Penetration Testing methodology.
As of April 2022, one of our founders who goes by the nickname of “bongo” managed to achieve 1st. rank amongst hundreds of security researches on Bug Bounty Hunter. Bug Bounty Hunter is a sophisticated modern web application with all kinds of vulnerabilities which have been found in real-world application bug hunting.
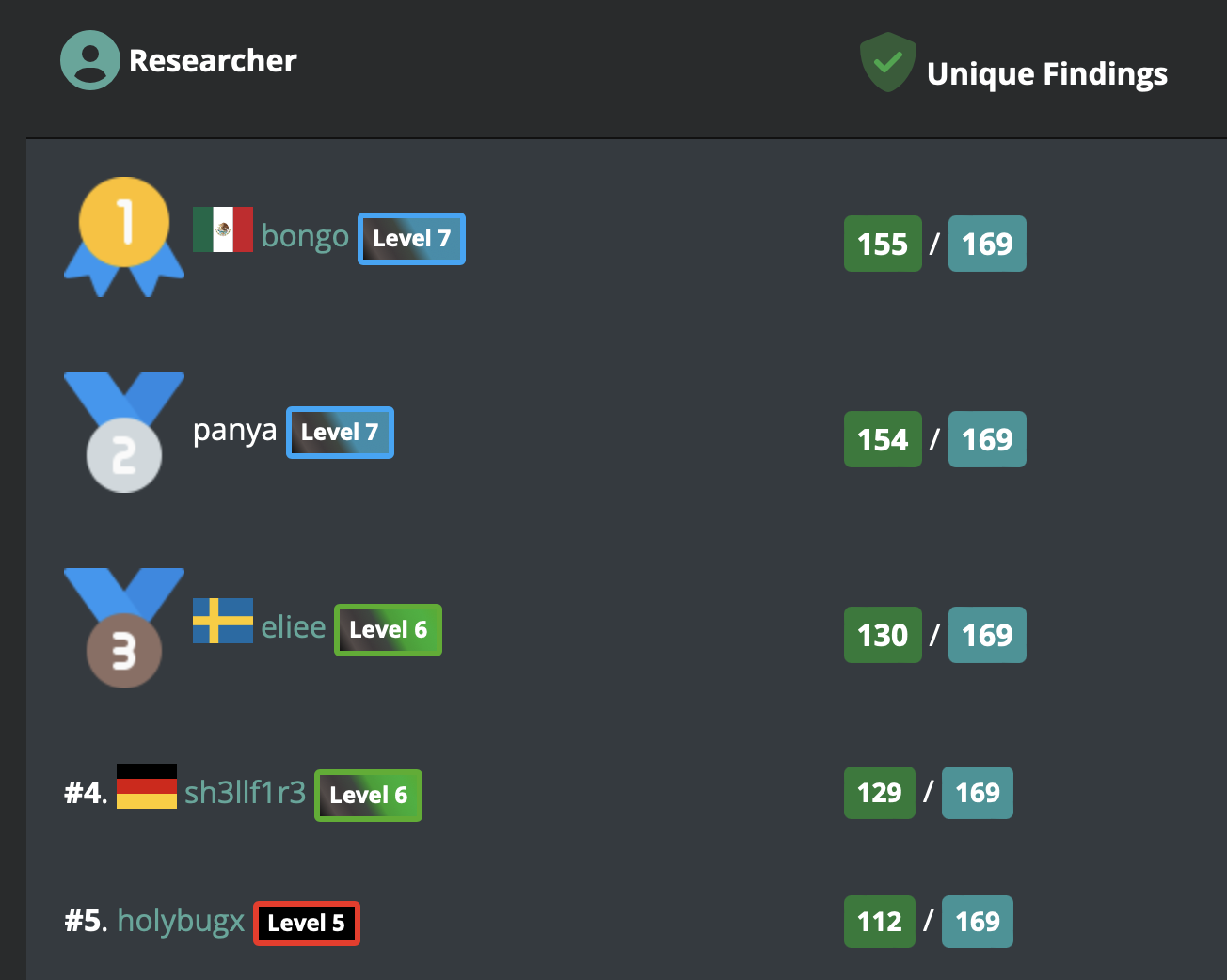
https://www.bugbountyhunter.com/hunter/bongo


